Caddy Could Be Leaking Your Secret Domains

You may be inadvertantly leaking the subdomains of your homelab for everyone to see on the internet.
It is generally illadvised to apply this advice to production serves or services not intended to be kept private/secret. The NSA wrote about this topic in Avoid Dangers of Wildcard TLS Certificates, the ALPACA Technique
There are many websites that monitor ssl certificate registers for new registrations and expose this information for all. One such website is https://crt.sh.
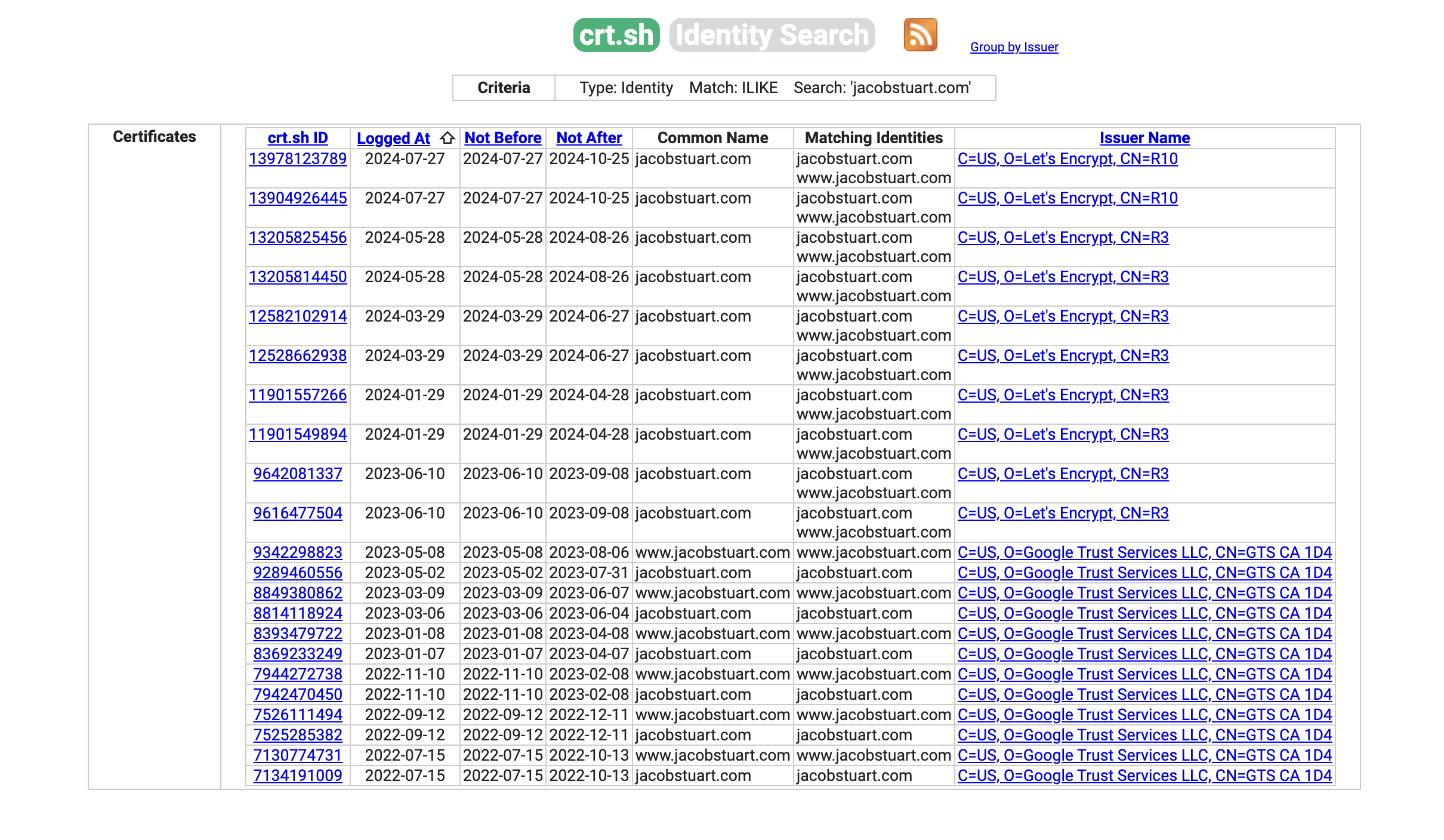
If you had a subdomain where your stored your secrets like secrets.example.com, it would appear on sites like this with the standard Caddy configuration.
To have Caddy always uses a wildcard certificate for all your domains, ensure each domain and subdomain in your Caddyfile as has a wildcard definition. For instance, if you already have definitions for secrets.example.com and moresecrets.team.example.com, you will need:
*.example.com {
respond "Access denied." 403
}
*.team.example.com {
respond "Access denied." 403
}
Let's Encrypt requires using the DNS Challenge to be able to use wildcards.